Secure Remote IoT P2P SSH On Windows 10: A Step-by-Step Guide
In an age where our lives are increasingly intertwined with the digital realm, and the Internet of Things (IoT) is no longer a futuristic concept but a present-day reality, can you truly afford to overlook the security of your interconnected devices?
Setting up secure connections for remote IoT devices on Windows 10 is not just a technical exercise; it's a fundamental necessity. It demands a meticulous approach, a keen eye for detail, and a commitment to best practices. This guide serves as your compass, navigating you through the complexities of establishing secure Peer-to-Peer (P2P) connections for your remote IoT devices using SSH on Windows 10. We'll delve into the tools, configurations, and essential knowledge needed to safeguard your data and ensure the stability of your connections.
Since the primary focus is on technical processes rather than an individual, here's a table outlining the essential components and considerations for securely connecting remote IoT devices:
| Category | Details | Explanation | Importance |
|---|---|---|---|
| Software Download & Installation | RemoteIoT Client | The initial step involves obtaining and installing the official RemoteIoT client software on your Windows 10 machine. This software serves as the primary interface for managing and connecting to your remote devices. | Provides the foundational software for managing remote IoT devices. |
| Security Settings Configuration | SSH Configuration, Authentication, Encryption | Within the RemoteIoT client, configure the security settings. This includes setting up Secure Shell (SSH) parameters such as port forwarding, enabling encryption, and implementing strong authentication methods. | Ensures data is protected during transmission and only authorized devices can access the network. |
| Connection Testing & Verification | Ping, SSH Connection Tests | After configuration, thoroughly test the connection to your remote IoT devices. Use tools like ping or SSH connection tests to verify that the connection is active, stable, and secure. | Confirms that the system is working properly, and the communication channel is established correctly. |
| P2P Network Understanding | Understanding P2P Architecture, Network Topology | Gaining a solid grasp of how P2P networks operate, along with the structure of your particular network topology, is vital. This understanding informs your configuration choices and troubleshooting efforts. | Understanding how devices connect directly, bypassing centralized servers, improves security and efficiency. |
| Encryption Protocols | AES, TLS/SSL | Utilizing encryption protocols such as Advanced Encryption Standard (AES) or Transport Layer Security/Secure Sockets Layer (TLS/SSL) is crucial for securing the data transmitted between your Windows 10 system and remote IoT devices. | Encryption renders data unreadable to unauthorized parties, significantly improving security. |
| Authentication Mechanisms | Password, Key-based Authentication, Multi-Factor Authentication | Employ robust authentication mechanisms to ensure only authorized devices and users can access the network. Consider password protection, key-based authentication, and, where feasible, multi-factor authentication (MFA). | Prevents unauthorized access to devices and networks. |
| Access Control | Firewall Rules, User Permissions | Implementing access control mechanisms, such as carefully configured firewall rules and restricted user permissions, helps in defining and managing who can access what within your IoT ecosystem. | Further restricts unauthorized access and potential security breaches. |
| Firewall Configuration | Inbound and Outbound Rules | Configuring your Windows 10 firewall correctly is essential. You'll need to create rules that allow traffic on the SSH port (typically port 22) while blocking all other unnecessary ports. | Controls network traffic and prevents unwanted access. |
| Regular Updates | Software Updates, Security Patches | Keep the RemoteIoT client, Windows 10 operating system, and any related software updated. This is an ongoing practice to protect against identified vulnerabilities. | Protects against the latest security threats and exploits. |
| Monitoring | Traffic Monitoring, Intrusion Detection | Monitor network traffic for unusual activity. Consider using intrusion detection systems (IDS) to detect and respond to potential security breaches. | Allows for quick identification and response to security incidents. |
| SSH Key Management | Key Generation, Secure Storage | If using SSH keys, ensure they are generated securely and stored in a safe location. Avoid storing private keys on your devices directly. | Prevents unauthorized access if a key is compromised. |
| Remote Device Security | Device Hardening, Firmware Updates | Ensure that the remote IoT devices themselves are secured. This includes changing default passwords, enabling encryption, and regularly updating the firmware. | Extends security to the connected devices. |
For more in-depth information on cybersecurity best practices, you can consult the National Institute of Standards and Technology (NIST) Cybersecurity Framework. Their guidelines provide a comprehensive approach to managing and mitigating cybersecurity risks. You can find more information on NIST Cybersecurity Framework.
The initial step on your journey to secure remote IoT device access involves obtaining and installing the RemoteIoT client on your Windows 10 machine. This application serves as the control center, managing the connection and data flow between your computer and the remote IoT devices. Download the software from the official RemoteIoT website. Be extremely cautious about the source of the software to avoid malicious downloads. Only trust the official website to get the client, which should be compatible with Windows 10.
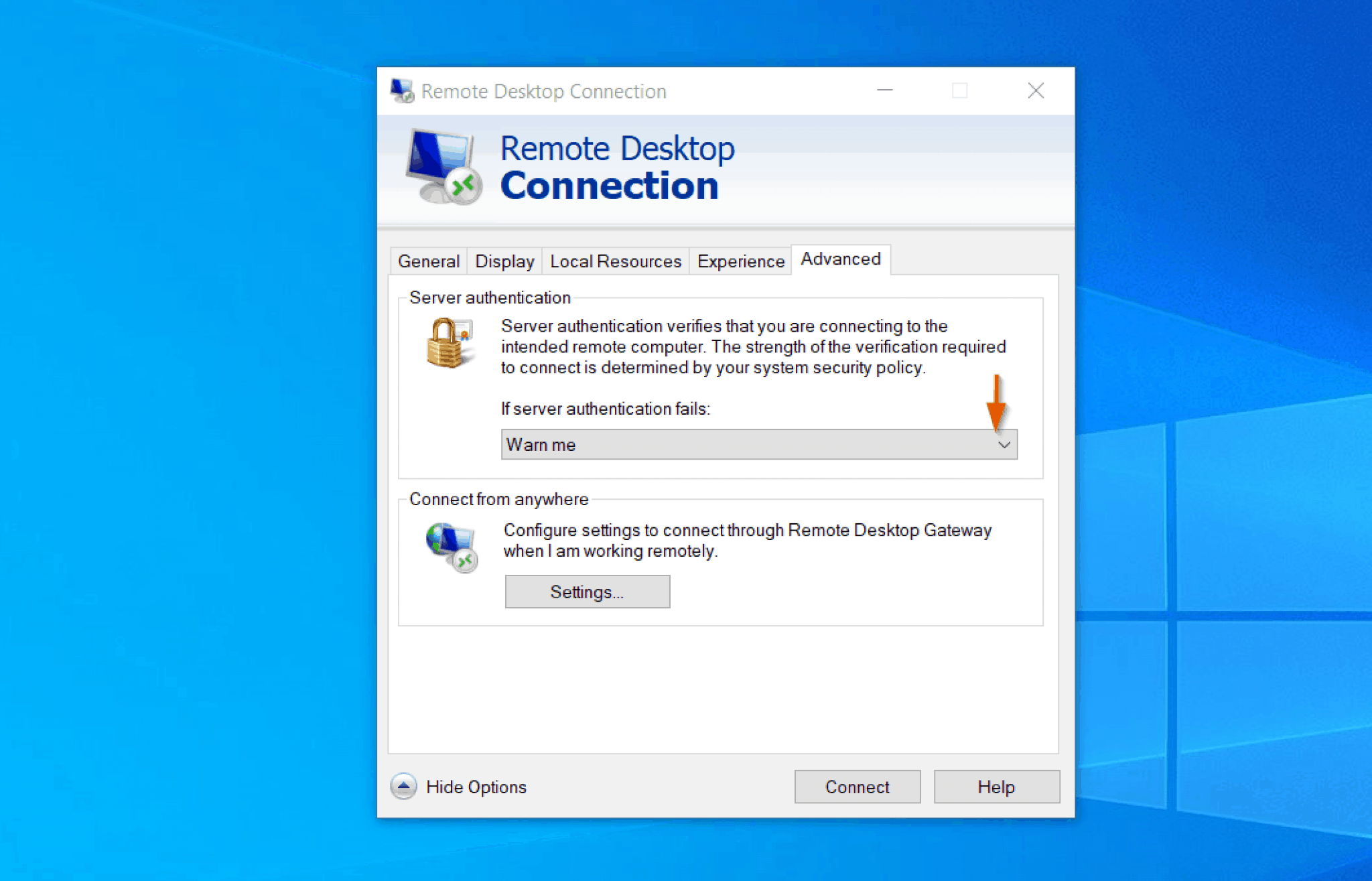
Once installed, configuring the security settings within the RemoteIoT client becomes paramount. These settings form the core of your secure connection. It's here you establish the SSH connection, enabling encryption, and implementing robust authentication protocols. This is where you define the parameters that ensure your data remains private and only authorized devices can access your network.
Securing your connections also involves thorough testing and verification. After configuring security settings, its essential to confirm everything is running as expected. Testing validates your settings. Tools like ping and SSH connection tests are invaluable in confirming that the connection to your remote IoT devices is active, stable, and, crucially, secure. These tests confirm that communication channels are correctly established and are functioning properly.
When dealing with remote IoT devices, the importance of secure connections cannot be overstated. In a P2P network, devices communicate directly, and without proper security measures, data can be vulnerable to interception. Its crucial to understand the role of SSH in protecting your data. SSH creates an encrypted channel, safeguarding your data in transit. It protects against eavesdropping and ensures that data remains confidential.
Setting up SSH on Windows 10 involves several key steps. You need to first download and install an SSH client, or leverage the built-in OpenSSH client if you have it enabled. Subsequently, you will configure the client with the correct IP address or hostname of your remote IoT device, as well as the correct port (typically port 22). Then, configure appropriate security settings, which usually involve SSH keys or passwords, or preferably, both. Remember, SSH keys enhance security over simple password authentication. This is the foundation for establishing a secure and reliable P2P connection with your IoT devices.
Remember, security is a continuous process, not a one-time setup. Regular software updates are crucial to patching vulnerabilities that may be exploited. Windows 10 and the RemoteIoT client should be kept updated to safeguard against the latest threats. Monitoring and access control also play a significant role. Monitoring your network traffic, identifying suspicious activity, and implementing strict access controls help maintain the integrity of your IoT ecosystem. This is not a task to be taken lightly in today's interconnected environment.
You will want to ensure you're downloading the RemoteIoT client from a trusted source, preferably the official website. The availability and reliability of free download options are a key consideration for many users. Be certain that any download is from an official or trusted source. Verifying the integrity of the downloaded software is vital for security. Be aware of the risks associated with downloading software from unofficial or untrusted sources. These sources can sometimes contain malware or other malicious software that could compromise your security.
Securing connections to Raspberry Pi devices over a P2P network requires a meticulous approach, especially for remote access. Using SSH enables a secure and encrypted communication channel, making it ideal for managing your Raspberry Pi remotely. Following a step-by-step guide ensures a smooth and secure setup process. Start by downloading and installing the necessary software on both your Windows 10 machine and the Raspberry Pi. Configure SSH, set up strong passwords, and consider SSH key authentication for an added layer of security. Test the connection thoroughly to verify the secure P2P connection.
The ability to securely connect remote IoT devices in a P2P network is a critical skill. By understanding the best practices, tools, and configurations outlined in this guide, you can confidently establish secure connections. Remember, a secure setup protects your data and allows you to manage your IoT ecosystem efficiently, allowing you to harness the full potential of the Internet of Things. Prioritize security and stay informed about the latest threats to keep your interconnected world safe.
In today's digital age, the ability to securely connect remote IoT devices via a P2P download on Windows 10 is a skill that is increasingly sought after by tech enthusiasts and professionals alike. This guide aims to equip you with the knowledge and best practices required for a robust setup. The main goal is to empower you with the knowledge to safeguard your data and manage your devices efficiently.


Detail Author:
- Name : Miss Zora Okuneva DDS
- Email : feest.lonnie@spinka.com
- Birthdate : 1999-12-10
- Address : 3366 Stacey Circle Kareemmouth, MO 22438-9026
- Phone : 1-351-538-8768
- Company : Thiel-Smith
- Job : Adjustment Clerk
- Bio : Sapiente fuga eum soluta eum dignissimos at voluptatem. Aut id id ut et voluptas et et. Velit necessitatibus quo natus sunt qui assumenda. Ut doloribus ipsum aut molestiae.