Secure Remote IoT: P2P SSH On Raspberry Pi & Free Download
In an age where connectivity reigns supreme, could you be overlooking a crucial aspect of your Internet of Things (IoT) setup? The ability to establish secure, direct connections between your devices, particularly those powered by a Raspberry Pi, is no longer optional its an absolute necessity. This is especially true when considering remote access, data security, and the need to manage devices regardless of their location or network configurations.
The rapid evolution of IoT has ushered in an era of interconnected devices, creating a demand for robust, secure, and efficient communication methods. This is where the concept of securely connecting remote IoT devices using p2p ssh, particularly on a Raspberry Pi, takes center stage. The promise of streamlined data transmission, minimized latency, and unparalleled security makes this a cornerstone for both tech enthusiasts and businesses alike. The core of this technology lies in its ability to bypass complex network configurations and intermediaries, providing a direct line of communication that is both swift and secure.
Let's delve deeper into the intricacies of securely connecting remote IoT devices using p2p SSH downloads. This exploration will cover a range of aspects, including the process of setting up secure connections, the advantages of utilizing SSH over other protocols, and the best practices for implementation. It's more than just a technical exercise; it's about equipping yourself with the knowledge to safeguard your devices and data in an increasingly interconnected world.
Understanding the technology's potential demands a clear understanding of its key components. Heres a breakdown of the critical elements involved:
The RemoteIoT p2p VPC network is the backbone, providing direct connections. It's engineered to minimize latency and maximize bandwidth, resulting in exceptionally fast data transfer. The advantage here is its direct, point-to-point communication, avoiding the bottlenecks that often plague traditional network configurations.
The process starts by installing the RemoteIoT service on any IoT device with a TCP/IP stack. This is where the service acts as the intermediary, enabling secure connections, and facilitating encrypted communication.
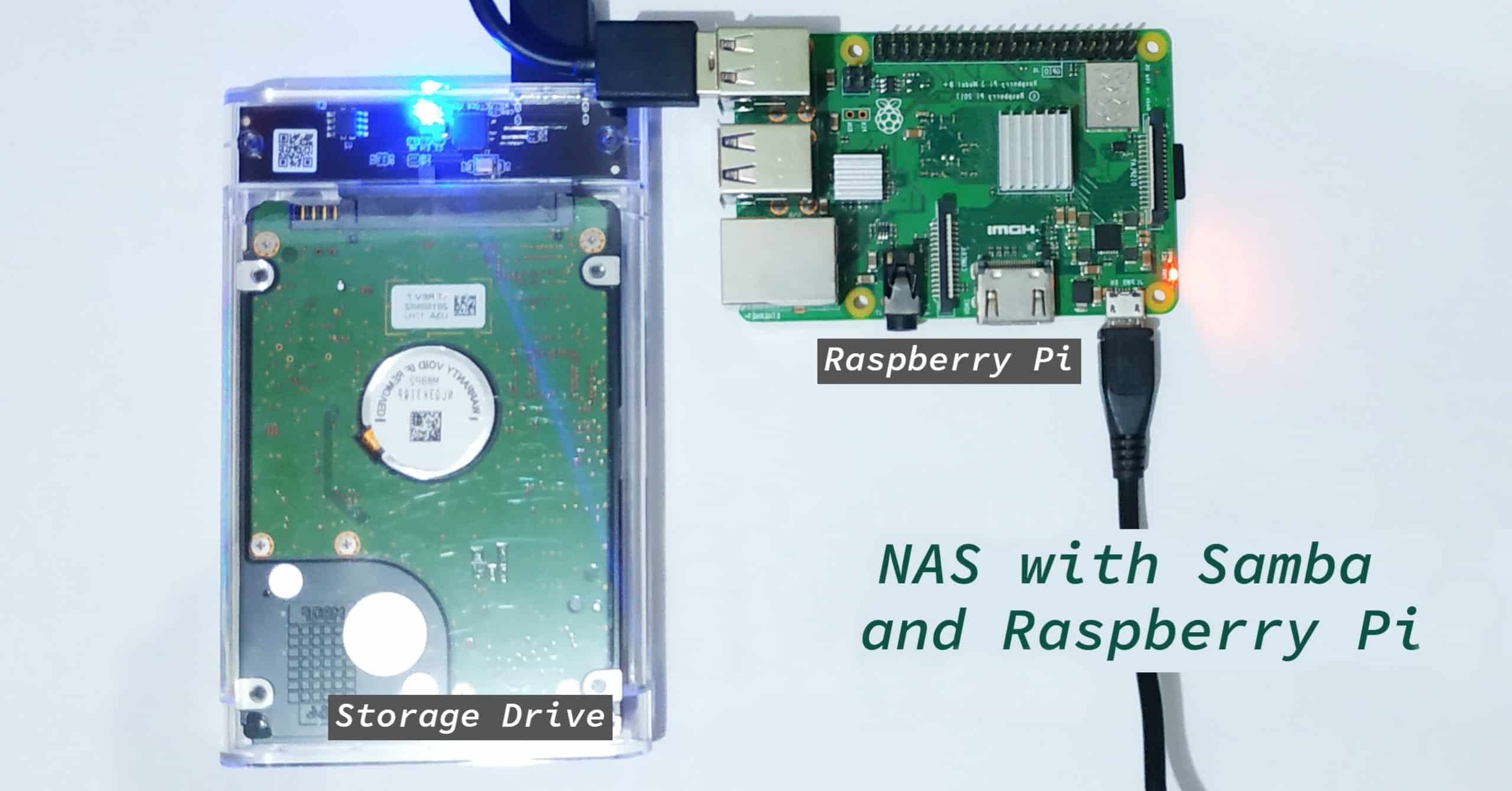
Then, consider a Raspberry Pi, a widely used, versatile, and affordable single-board computer. The need to securely connect a Raspberry Pi to the internet is essential for remote access and IoT applications, expanding the accessibility of your devices.
Now, here comes the main part, the RemoteIoT p2p free download is not just a download, its your gateway to simplified IoT connectivity. It empowers users to manage and control their devices remotely, without the complexity of setting up complex network configurations.
To enable this functionality, SSH tunnels are a critical component. All network traffic is encrypted through an SSH tunnel, thereby ensuring confidentiality. Not even the RemoteIoT platform can intercept or interpret the data transmitted through the tunnel, providing an extra layer of security.
The following table will provide you a roadmap of the tools and software that you should be aware of when connecting to an IoT device. This guide provides users with the tools, download links, and essential software necessary to establish secure connections.
| Component | Description | Function | Download/Link |
|---|---|---|---|
| RemoteIoT Service | The software agent installed on the IoT device. | Facilitates secure, direct p2p connections. | Download link (example): [Placeholder Link - replace with actual RemoteIoT download link] |
| SSH Client | A tool to establish a secure shell connection. | Encrypts and secures the communication channel. | Examples: OpenSSH (Linux/macOS), PuTTY (Windows) |
| Raspberry Pi OS | Operating system for Raspberry Pi. | Controls and manages the Raspberry Pi hardware. | Raspberry Pi OS download |
| Android App (if applicable) | Mobile application for remote management. | Allows remote access and control from a smartphone. | [Placeholder - link to potential Android app, if available] |
| Firewall Configuration | Rules to allow incoming and outgoing traffic. | Ensures only authorized connections are allowed. | Varies based on device/OS. Generally involves opening specific ports. |
The core of RemoteIoT's functionality lies in the establishment of a peer-to-peer (p2p) virtual private cloud (VPC) network. This network is designed to provide direct connections between IoT devices, ensuring data communication is as fast as possible, with minimal latency and high bandwidth. The critical advantage here is the elimination of unnecessary hops and intermediaries, which often introduce delays and security vulnerabilities in traditional networking setups. The architecture is built to provide robust solutions tailored to your needs, streamlining operations whether you are a tech enthusiast or a business owner looking to optimize processes.
The ability to securely connect remote IoT devices is a critical component in today's connected world. The availability of a RemoteIoT p2p free download provides users with a gateway to smooth IoT connectivity, which permits users to manage and control devices remotely. This is incredibly important because it simplifies access, which provides the flexibility and security that are vital.
One of the main advantages of RemoteIoT lies in its capacity to overcome network restrictions such as firewalls and NAT (Network Address Translation). The service is designed to allow you to access and manage your Raspberry Pi remotely, even when it is behind these security layers, providing a level of accessibility unmatched by conventional methods.
For those eager to venture into this domain, the process starts with a free download. The software allows easy setup of secure, direct connections between devices. It eliminates complex configurations or intermediaries, making the process accessible even for those without extensive networking expertise. The download itself is a gateway to a world where you can manage and control your devices remotely with ease.
The benefits of employing SSH over other protocols are substantial. SSH offers strong encryption, protecting data from unauthorized access. Its support for port forwarding enables the tunneling of traffic through firewalls. Further, it provides a secure channel for remote access and management, essential for the secure operation of IoT devices.
The concept of a securely connect remote IoT p2p download represents a pivotal evolution in contemporary networking. It is not merely a technical upgrade, but a strategic necessity in a society that relies increasingly on the interconnection of devices. This evolution is reshaping the landscape of remote device management and data security, making it more streamlined and secure.
Best practices for securing your remote IoT devices include using strong passwords, regular software updates, and enabling two-factor authentication where possible. It's also critical to monitor network traffic for suspicious activity and establish a clear security policy. Secure configuration is key to protecting your devices and data. Consider using the latest encryption standards and keeping your systems up to date with the most recent security patches.
The concept of secure remote IoT connectivity has transformed from a mere advantage to a critical requirement in the modern networking landscape. The RemoteIoT platform provides a comprehensive solution, allowing you to securely connect and manage machines and devices from any location, while taking into consideration network setups. This empowers you to retain full control over your devices, ensuring that your operations continue without interruption.
The core of this architecture revolves around the SSH tunnel. All network traffic is encrypted through this tunnel, ensuring that data is protected from unwanted access. With this in place, not even the RemoteIoT platform can read the data. This provides an essential level of security, giving users the peace of mind that their sensitive information is safe and secure.
Looking ahead, the continuing integration of IoT will demand even more robust and secure networking methods. The deployment of p2p SSH on a Raspberry Pi and utilizing appropriate downloads is at the forefront of modern device management. As technology evolves, the need for secure, direct connections will only increase, making this approach essential for anyone involved in IoT applications.
In conclusion, the significance of securely connecting remote IoT devices using p2p SSH on a Raspberry Pi has become a requirement rather than a luxury in today's world. As we have explored the intricacies of secure connections, the benefits of SSH, and best practices, it's clear that this approach is vital for both tech enthusiasts and enterprises. The ability to manage your devices securely and remotely, without complexities, is not just practical it's a strategic necessity.
The provided content forms a solid foundation for understanding the benefits and mechanisms of securing remote IoT devices, particularly within the context of a Raspberry Pi setup. The key takeaway is that secure, direct connections are fundamental, offering a level of control and security that is critical in today's interconnected environment.


Detail Author:
- Name : Miss Zora Okuneva DDS
- Email : feest.lonnie@spinka.com
- Birthdate : 1999-12-10
- Address : 3366 Stacey Circle Kareemmouth, MO 22438-9026
- Phone : 1-351-538-8768
- Company : Thiel-Smith
- Job : Adjustment Clerk
- Bio : Sapiente fuga eum soluta eum dignissimos at voluptatem. Aut id id ut et voluptas et et. Velit necessitatibus quo natus sunt qui assumenda. Ut doloribus ipsum aut molestiae.