Secure Remote IoT With Raspberry Pi & AWS VPC: A Step-by-Step Guide
Are you ready to fortify your Internet of Things (IoT) projects against the ever-present threats of the digital world? Securing your remote IoT devices, especially those powered by Raspberry Pi and connected to Amazon Web Services (AWS), is no longer optional; it's a fundamental necessity.
The burgeoning landscape of IoT presents unparalleled opportunities, from smart homes to industrial automation, but with these advancements comes the urgent need for robust security measures. Neglecting the security of your connected devices exposes your network to potential breaches, data leaks, and malicious attacks. This guide serves as your comprehensive roadmap to navigate the intricate process of establishing a secure connection between your remote IoT devices, specifically Raspberry Pi, and an AWS Virtual Private Cloud (VPC).
The key to successfully integrating your Raspberry Pi with an AWS VPC lies in a strategic, layered approach to security. This encompasses several crucial steps, including configuring your VPC, designing secure subnets and route tables, setting up effective security groups, and, critically, establishing a secure tunnel for communication. Let's dive into the specifics.
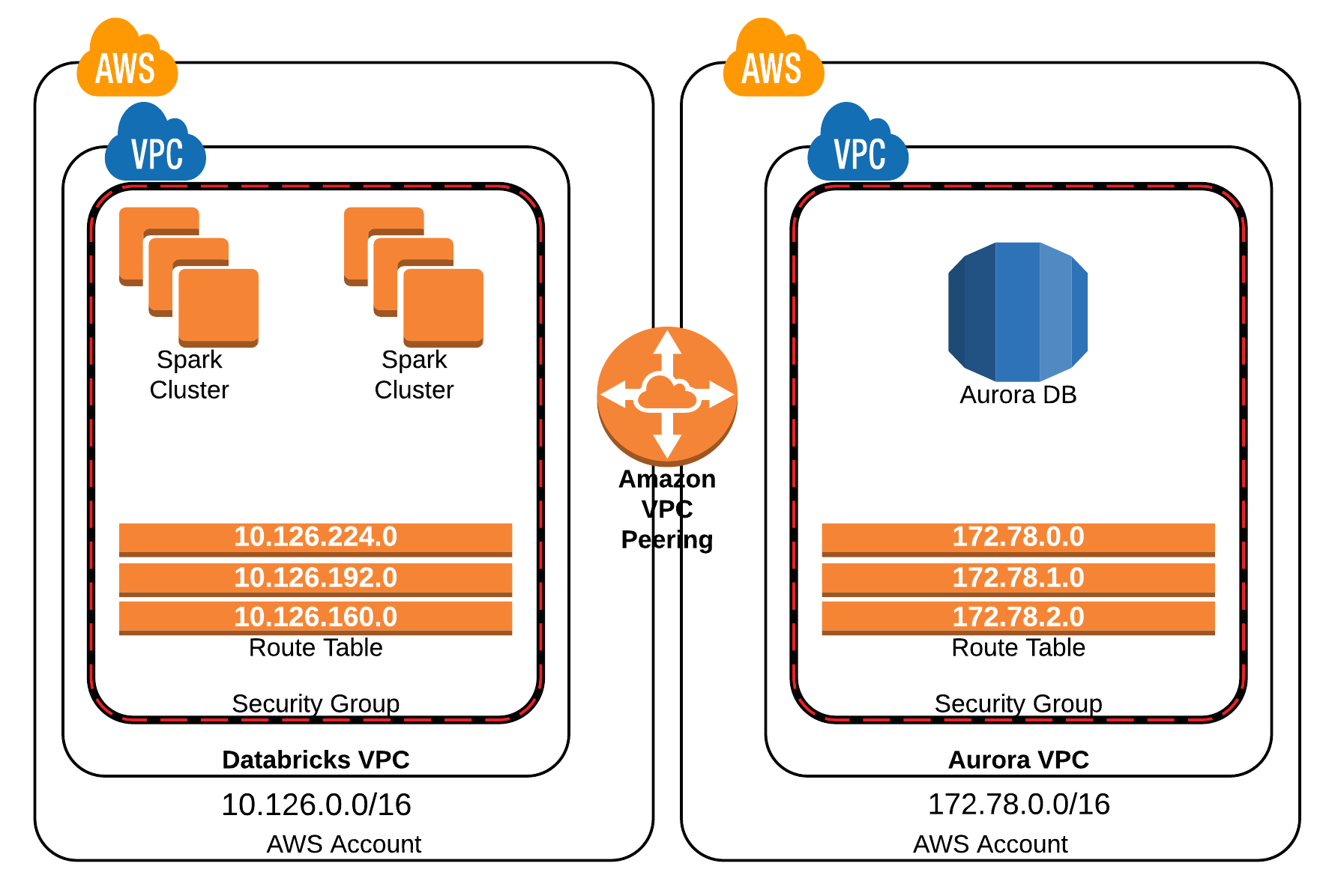
First and foremost, you must establish a Virtual Private Cloud (VPC) within your AWS environment. A VPC is essentially a logically isolated section of the AWS cloud, providing you with the control to launch your resources into a virtual network that you define. When creating your VPC, carefully consider the IP address range (CIDR block) you will use. This will define the scope of your private network within AWS.
Within your VPC, subnets play a pivotal role. Subnets divide your VPC's IP address range into smaller segments. It's crucial to define public and private subnets. Public subnets are designed for resources that require direct internet access, while private subnets are for resources that need to be isolated from the internet. Place your Raspberry Pi devices within a private subnet for enhanced security, and utilize a secure tunnel or VPN to access them.
Route tables act as traffic directors within your VPC. They dictate where network traffic is sent. Each subnet is associated with a route table, which determines how traffic is routed between the subnets and to external networks, such as the internet or your on-premises network. Configuring these tables correctly is crucial for directing traffic to the right destinations and ensuring secure communication.
Security groups are virtual firewalls for your resources. They control the inbound and outbound traffic for your resources, such as your Raspberry Pi instances. By defining specific rules, you can permit only authorized traffic to reach your Raspberry Pi. This includes limiting the ports that are open and the IP addresses that can connect, providing an essential layer of defense against unauthorized access.
Establishing a secure tunnel is the cornerstone of secure communication. This typically involves setting up a VPN connection or using technologies like AWS Site-to-Site VPN or a more cost-effective solution can be created using tools like OpenVPN. This creates an encrypted connection between your remote device and your VPC, protecting your data in transit and ensuring secure remote access to your Raspberry Pi and other IoT devices.
RemoteIoT is a platform that simplifies the management and secure connection of IoT devices to cloud environments like AWS VPC. It streamlines the complexities involved in establishing and maintaining secure connections, making it an excellent choice for your projects. Employing platforms like these can streamline the process and ensure your IoT devices are securely integrated and managed.
Connecting your Raspberry Pi to an AWS server via a virtual private cloud (VPC) is a powerful method for remote IoT device management. It provides the advantage of securely controlling your devices, all while scaling your project.
The following table outlines the essential steps involved in the secure connection process. Each step is vital, from VPC setup to securing your devices with appropriate security protocols.
By implementing these steps, you create a robust and secure IoT environment that fits your project's needs. The combination of a properly configured VPC, secured network components, and the deployment of secure tunneling will safeguard your data and ensure reliable device functionality. Remember, a commitment to security is vital for any IoT project. This is essential for the modern connected world.
Securing a stable connection between your remote IoT devices and AWS in a Windows environment, for example, requires careful consideration. You'll want to review troubleshooting steps and best practices to avoid common issues and maintain a seamless experience. Whether you're a seasoned network engineer or a tech enthusiast, a strong understanding of the process is essential to safeguard sensitive information and protect system integrity.
As the Internet of Things (IoT) continues to flourish, connecting remote IoT devices within a virtual private cloud (VPC) on AWS has become a critical business requirement. With the rise of smart devices, the demand for secure, scalable, and efficient IoT solutions has led to the emergence of platforms like RemoteIoT. This platform bridges the gap between edge devices and cloud infrastructure, providing a reliable system to keep your devices connected.
Securely connecting remote IoT devices to AWS VPC is one of the most common challenges. By combining the flexibility of Raspberry Pi with AWS's advanced cloud infrastructure, businesses and hobbyists can create a reliable and secure IoT ecosystem. Whether you're monitoring sensors, automating tasks, or building a smart home system, this guide will walk you through the process of securely connecting your Raspberry Pi to an AWS VPC.
Let's discuss some frequently asked questions:
Q: What is "Securely connecting remote IoT VPC Raspberry Pi AWS"?
A: Securely connecting remote IoT VPC Raspberry Pi AWS refers to the process of integrating a Raspberry Pi device with Amazon Web Services (AWS) through a Virtual Private Cloud (VPC) while leveraging RemoteIoT for secure communication. In essence, its about making sure your Raspberry Pi can securely communicate with your AWS resources.
Q: Why is secure connection important?
A: Secure connection is essential for the following reasons:
- Data Protection: Ensures that data transmitted between your Raspberry Pi and the cloud is encrypted and protected from unauthorized access.
- Device Security: Prevents unauthorized access to your Raspberry Pi, protecting it from malicious attacks and potential compromise.
- Compliance: Helps you meet regulatory requirements for data security and privacy.
- System Integrity: Maintains the overall integrity and reliability of your IoT system.
- Confidentiality: Safeguarding sensitive data and ensuring device functionality is the paramount importance for secure connection
Q: What exactly is "securely connecting remote IoT VPC Raspberry Pi AWS" mean?
A: It is the process of linking your Raspberry Pi device to a secure, isolated network (VPC) hosted on Amazon Web Services (AWS). This allows your device to access cloud services and exchange data securely.
Now, let's get down to the core of the matter: implementing the secure connection.
When we talk about securely connecting remote IoT devices using Raspberry Pi and AWS, we are referring to a setup where your IoT devices are connected to a virtual private cloud (VPC) hosted on Amazon Web Services. A secure connection is not just a technical challenge; it's a necessity for protecting sensitive data and ensuring device functionality.
In conclusion, establishing a secure and reliable connection for your remote IoT devices, particularly when using a Raspberry Pi with AWS, requires careful planning, meticulous execution, and a steadfast commitment to security best practices. By following the steps outlined in this guide and remaining vigilant about emerging threats, you can create an IoT ecosystem that is both powerful and protected, ready to meet the challenges and opportunities of the digital age.


Detail Author:
- Name : Kaylie O'Conner
- Email : hills.gayle@hand.info
- Birthdate : 2001-05-26
- Address : 7160 Stehr Views Suite 073 North Angusshire, HI 76571
- Phone : +1 (248) 399-6451
- Company : Lakin-Collier
- Job : Well and Core Drill Operator
- Bio : Quis et veniam et maxime unde enim eius. Ea non expedita vel. Voluptatem eligendi architecto ex rerum rerum ea dignissimos.